Has your WordPress website been hacked?
Hackers will often install a backdoor to make sure they can get back in even after you secure your website. Unless you can remove that backdoor, there’s no stopping them.
In this article, we’ll show you how to find a backdoor in a hacked WordPress site and fix it.
How to Tell if Your Website Has Been Hacked
If you are running a WordPress website, then you need to take security seriously. That’s because websites are attacked an average of 44 times every day.
You can learn best practices to keep your site safe in our ultimate WordPress security guide.
But what if your site has already been hacked?
Some signs your WordPress site has been hacked include a drop in website traffic or performance, added bad links or unknown files, a defaced home page, an inability to log in, suspicious new user accounts, and more.
Cleaning up a hacked website can be incredibly painful and difficult. We take you through the process step by step in our beginner’s guide to fixing your hacked WordPress site. You should also make sure you scan your site for any malware that the hackers left.
And don’t forget to close the backdoor.
A smart hacker knows that you’ll eventually clean up your website. The first thing they might do is install a backdoor, so they can sneak back in after you secure the front door to your WordPress website.
What Is a Backdoor?
A backdoor is code added to a website that allows a hacker to access the server while remaining undetected, and bypassing the normal login. It allows a hacker to regain access even after you find and remove the exploited plugin or vulnerability to your website.
Backdoors are the next step of a hack after the user has broken in. You can learn how they may have done that in our guide on how WordPress sites get hacked and how to prevent it.
Backdoors often survive WordPress upgrades. That means your site will remain vulnerable until you find and fix every backdoor.
How Do Backdoors Work?
Some backdoors are simply hidden admin usernames. They let the hacker log in as normal by typing a username and password. Because the username is hidden, you’re not even aware that someone else has access to your website.
More complex backdoors can allow the hacker to execute PHP code. They manually send the code to your website using their web browser.
Others have a full fledged user interface that allows them to send emails as your WordPress hosting server, execute SQL database queries, and much more.
Some hackers will leave more than one backdoor file. After they upload one, they will add another to ensure their access.
Where Are Backdoors Hidden?
In every case we’ve found, the backdoor was disguised to look like a WordPress file. The code for backdoors on a WordPress site are most commonly stored in the following locations:
- A WordPress theme, but probably not the the one you’re currently using. Code in a theme is not overwritten when you update WordPress, so it’s a good place to put a backdoor. That’s why we recommend deleting all inactive themes.
- WordPress plugins are another good place to hide a backdoor. Like themes, they’re not overwritten by WordPress updates, and many users are reluctant to upgrade plugins.
- The uploads folder may contain hundreds or thousands of media files, so it’s another good place to hide a backdoor. Bloggers almost never check its contents because they just upload an image and then use it in a post.
- The wp-config.php file contains sensitive information used to configure WordPress. It’s one of the most highly targeted files by hackers.
- The wp-includes folder contains PHP files required for WordPress to run properly. It’s another place that we find backdoors because most website owners don’t check to see what the folder contains.
Examples of Backdoors We’ve Found
Here are some examples of where hackers have uploaded backdoors. In one site we cleaned up, the backdoor was in the wp-includes folder. The file was called wp-user.php, which looks innocent enough, but that file doesn’t actually exist in a normal WordPress installation.
In another instance, we found a PHP file named hello.php in the uploads folder. It was disguised as the Hello Dolly plugin. What’s strange is that the hacker put it in the uploads folder instead of the plugins folder.
We’ve also found backdoors that don’t use the .php file extension. One example was a file named wp-content.old.tmp, and we’ve also found backdoors in files with a .zip extension.
As you can see, hackers can take very creative approaches when hiding a backdoor.
In most cases, the files were encoded with Base64 code that can perform all sorts of operations. For example, they can add spam links, add additional pages, redirect the main site to spammy pages, and more.
With that being said, let’s take a look at how to find a backdoor in a hacked WordPress site and fix it.
How to Find a Backdoor in a Hacked WordPress Site and Fix It
Now you know what a backdoor is and where it might be hidden. The difficult part is finding it! After that, cleaning it up is as easy as deleting the file or code.
1. Scan for Potentially Malicious Code
The easiest way to scan your website for backdoors and vulnerabilities is with a WordPress malware scanner plugin. We recommend Sucuri because it helped us block 450,000 WordPress attacks in 3 months, including 29,690 backdoor related attacks.
They offer a free Sucuri security plugin for WordPress that lets you scan your website for common threats and harden your WordPress security. The paid version includes a server side scanner that runs once each day and looks for backdoors and other security issues.
A great alternative to Sucuri is MalCare, which has an automated malware removal feature. This will remove all malware files, including backdoors, from your website.
Learn more in our guide on how to scan your WordPress site for potentially malicious code.
2. Delete Your Plugins Folder
Searching through your plugin folders looking for suspicious files and code is time consuming. And because hackers are so sneaky, there’s no guarantee you will find a backdoor.
The best thing you can do is delete your plugins directory, and then reinstall your plugins from scratch. This is the only way to know for sure that there are no backdoors in your plugins.
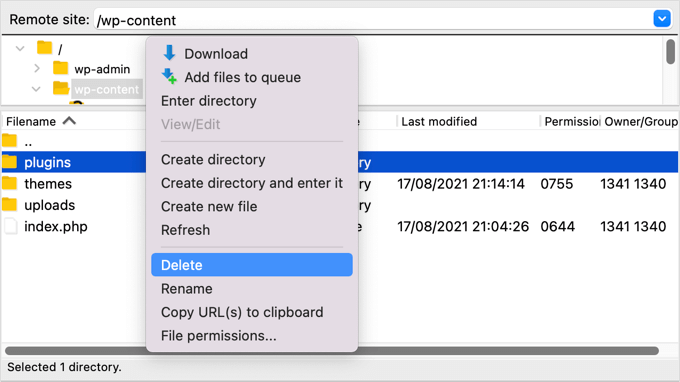
You can access your plugins directory using an FTP client or your WordPress host’s file manager. If you haven’t used FTP before, then you may want to see our guide on how to use FTP to upload files to WordPress.
You will need to use the software to navigate to your website’s wp-content folder. Once there, you should right click on the plugins folder and select ‘Delete’.
3. Delete Your Themes Folder
In the same way, instead of spending time searching for a backdoor among your theme files, it’s better just to delete them.
After you delete your plugin folder, simply highlight the themes folder and delete it in the same way.
You don’t know whether there was a backdoor in that folder, but if there was, it’s gone now. You just saved time and you eliminated an extra point of attack.
Now you can reinstall any themes that you need.
4. Search the Uploads Folder for PHP Files
Next, you should take a look through the uploads folder and make sure that there are no PHP files inside.
There is no good reason for a PHP file to be in this folder because it’s designed to store media files such as images. If you find a PHP file there, then it should be deleted.
Like the plugins and themes folders, you’ll find the uploads folder in the wp-content folder. Inside the folder you will find multiple folders for each year and month you have uploaded files. You will need to check each folder for PHP files.
Some FTP clients offer tools that will search the folder recursively. For example, if you use FileZilla, then you can right click the folder and select ‘Add files to queue’. Any files found in any subdirectories of the folder will be added to the queue in the bottom pane.
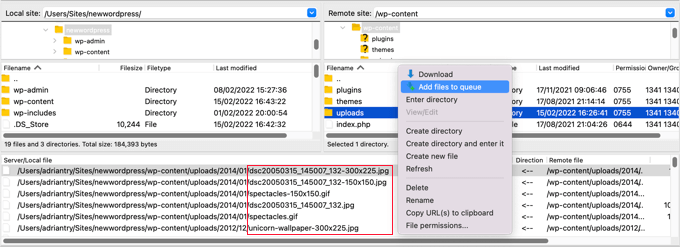
You can now scroll through the list looking for files with the .php extension.
Alternatively, advanced users who are familiar with SSH can write the following command:
find uploads -name "*.php" -print
5. Delete the .htaccess File
Some hackers may add redirect codes to your .htaccess file that will send your visitors to a different website.
Using an FTP client or file manager, simply delete the file from your website’s root directory, and it will be recreated automatically.
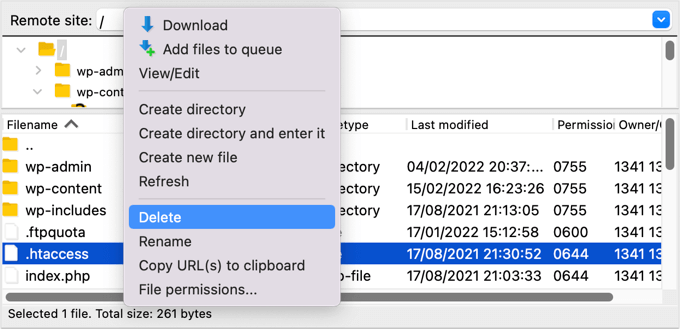
If for some reason it isn’t recreated, then you should go to Settings » Permalinks in your WordPress admin panel. Clicking the ‘Save Changes’ button will save a new .htaccess file.
6. Check the wp-config.php File
The wp-config.php file is a core WordPress file that contains information that allows WordPress to communicate with the database, the security keys for your WordPress installation, and developer options.
The file is found in your website’s root folder. You can view the file’s contents by selecting the Open or Edit options in your FTP client.
Now you should look at the contents of the file carefully to see if there is anything that looks out of place. It might be helpful to compare the file with the default wp-config-sample.php file which is located in the same folder.
You should delete any code that you’re certain doesn’t belong.
7. Restore a Website Backup
If you have been making regular backups of your website and are still concerned that your website isn’t completely clean, then restoring a backup is a good solution.
You will need to completely delete your website and then restore a backup that was taken before your website was hacked. This isn’t an option for everyone, but it will leave you 100% confident that your site is safe.
For more information, see our beginner’s guide on how to restore WordPress from backup.
How to Prevent Hacks in the Future?
Now that you’ve cleaned up your website, it’s time to improve your site’s security to prevent hacks in the future. It doesn’t pay to be cheap or apathetic when it comes to website security.
1. Regularly Backup Your Website
If you don’t already make regular backups of your website, then today is the day to start.
WordPress does not come with a built-in backup solution. However, there are several great WordPress backup plugins which allow you to automatically backup and restore your WordPress website.
Duplicator is one of the best WordPress backup plugins. It allows you to setup automatic backup schedules and will help you restore your WordPress site if something bad happens.

There’s also a free version of Duplicator you can use to create manual backups.
For step-by-step instructions, see our guide on how to backup your WordPress site with Duplicator.
2. Install a Security Plugin
You can’t possibly monitor everything that goes on your website when you’re busy working on your business. That’s why we recommend you use a security plugin like Sucuri.
We recommend Sucuri because they’re good at what they do. Major publications like CNN, USA Today, PC World, TechCrunch, The Next Web, and others agree. Plus, we rely on it ourselves to keep WPBeginner secure.
3. Make WordPress Login More Secure
It’s also important that you make your WordPress login more secure. The best way to start is to enforce the use of strong passwords when users create an account on your website. We also recommend you start using a password manager utility like 1Password.
The next thing you should do is add two-factor authentication. This will protect your website against stolen passwords and brute force attacks. It means that even if a hacker knows your username and password, they still won’t be able to log in to your website.
Finally, you should limit login attempts in WordPress. WordPress allows users to enter passwords as many times as they want. Locking a user out after five failed login attempts will significantly reduce a hacker’s chance of working out your login details.
4. Protect Your WordPress Admin Area
Protecting the admin area from unauthorized access allows you to block many common security threats. We have a long list of tips on how you can keep WordPress admin safe.
For example, you can password protect the wp-admin directory. This adds another layer of protection to the most important entry point to your website.
You can also limit access to the admin area to the IP addresses used by your team. This is another way to lock out hackers who discover your username and password.
5. Disable Theme and Plugin Editors
Did you know that WordPress comes with a built-in theme and plugin editor? This plain text editor allows you to edit your theme and plugin files directly from the WordPress dashboard.
While this is helpful, it can lead potential security issues. For example, if a hacker breaks into your WordPress admin area, then they can use the built-in editor to gain access to all your WordPress data.
After that, they will be able to distribute malware or launch DDoS attacks from your WordPress website.
To improve WordPress security, we recommend removing the built-in file editors completely.
6. Disable PHP Execution in Certain WordPress Folders
By default, PHP scripts can be run in any folder on your website. You can make your website more secure by disabling PHP execution in folders that don’t need it.
For example, WordPress never needs to run code stored in your uploads folder. If you disable PHP execution for that folder, then a hacker won’t be able to run a backdoor even if they successfully uploaded one there.
7. Keep Your Website Up to Date
Every new version of WordPress is safer than the previous one. Whenever a security vulnerability is reported, the core WordPress team works diligently to release an update that fixes the issue.
This means that if you are not keeping WordPress up to date, then you are using software with known security vulnerabilities. Hackers can search for websites running the older version and use the vulnerabilty to gain access.
That’s why you should always use the latest version of WordPress.
Don’t just keep WordPress up to date. You need to make sure that you also keep your WordPress plugins and themes current.
We hope this tutorial helped you learn how to find and fix a backdoor in a hacked WordPress website. You may also want to learn how to move WordPress from HTTP to HTTPS, or check out our list of WordPress errors and how to fix them.
If you liked this article, then please subscribe to our YouTube Channel for WordPress video tutorials. You can also find us on Twitter and Facebook.




Syed Balkhi says
Hey WPBeginner readers,
Did you know you can win exciting prizes by commenting on WPBeginner?
Every month, our top blog commenters will win HUGE rewards, including premium WordPress plugin licenses and cash prizes.
You can get more details about the contest from here.
Start sharing your thoughts below to stand a chance to win!
Jiří Vaněk says
It is also very good practice to contact the web server provider. They often have sophisticated malware detection tools and are able to scan the entire web and send a dump of infected files. This is what I would possibly recommend doing any time a website hacking problem turns out to be true. A provider can help a lot with this if they have good customer support.
Paul Booker says
If you have version control installed on your web server –– it is possible to very quickly determine if any of your files have changed, or additional files have been added, by running a simple command in your shell terminal.
If you are using Git for version control you just need to type “git status” into your shell terminal, to find out what has been hacked. You can the delete all of the changes with one command “git checkout — .”
If you don’t have version control you can basically just write a simple command “list all files modified in the last 7 days” which would be “find ./ -type f -mtime -7” and again you can find out what has been hacked. You can then manually delete the changes.
WPBeginner Support says
While possible, that is not a beginner friendly method so we do not recommend it for most users.
Admin
Vivek Tripathi says
Hello Sir in our maximum sites there was malicious codes injected but I Haven’t find these anywhere in database. In my all sites there was automatically malicious pages generated and it will shown on google and these pages were not shown in my wordpress dashboard and in posts sections.
Please Help me to find codes and get secured from this hacking I have losted many traffic from my WordPress site.
Please Help Me!
WPBeginner Support says
Hi Vivek,
Please see our article on how to clean a hacked WordPress site.
Admin
Abraham says
This is really the BEST post there is about “unhacking” your website, I don’t know if it worked completely with my site but I really do hope so.
Thanks so much guys!!
Azwan Abdullah says
Hi! I need some opinion. I’ve enabled open registration and set the default role as subscriber. From my understanding, this role can only have read capabilities. Means that they can only read posts on my blog, and comments. Am I right?
The purpose I’m doing this because I want to allow only registered people to comment. Ironically, I’m using some live traffic logger, which can track requests in to or out of my website. I noticed that the registered user is using anonymous IP from TOR network. They seems registering by accessing the register page directly, not by usual means.
Therefore, is it usually safe to let them? Does they (subscriber) has the capability to upload something on uploads or any folder on system? Since they can also have limited access to admin dashboard, can view wp version, is it considerably safe?
I hope someone and wpbeginner staff can respond these. Thanks in advance.
WPBeginner Support says
Hi Azwan,
You need to protect your website from spam user registrations.
Admin
Pradeep Gauda says
Hi ,
I found my word press website title changed by some hacker group as they mentioned . So checked my security plugins wordfence , did the scan but nothing found . How can they affecting the page title continue and what should i do for that .
Colin says
Hi
Sucuri & WP Clone uses the Uploads folder so what are we suppose to do there?
Also Exploit Scanner is coming up with loads of files that it doesn’t recognise and the plugin is up to date. Maybe the algorithm is not up to date with the latest version of WordPress so deleted it.
Sucuri has found no problems but it is the free version, Wordfence have found no errors either so I don’t trust Exploit Scanner at the moment.
Colin
Jo says
Thank you for a very informative and helpful article. I was able to finally understand what happened to my website ( thousands of malicious index.php files).
I avoided having to pay an extortion price to sitelock to repair my site, by simply installing a (clean) backup.
And now, I will make sure to install hundreds of antivirus plugins. Had not realised that my webhost bluehost did not include any basic level of security.
Mehreen says
Hi,
I understand this article is quite old now, but I’ll comment and try if I get response.
My site was recently compromised and after using free Sucuri, I switched to Wordfence. The latter helped me track all my files containing malicious code. No particular reason to not use Sucuri, I was just trying different options.
What are your views on wordfence vs sucuri? Paid versions.
Thanks.
WPBeginner Support says
Hi Mehreen,
They both offer good security. We recommend Sucuri because they offer cloud based website application firewall, which not only protects your website but also improves performance. Wordfence offers an application level firewall which runs on your server. See our article on best WordPress firewall plugins for more details.
Admin
Mohammed Jaid Ansari says
Hi
When i type my website address it will open and after some time he will redirect to other website. and in mobile when i type my website address directly he will redirect to google play store. and google also showing this website may be hacked. how i can solved this problem.
WPBeginner Support says
Hi,
See our guide on how to clean a hacked WordPress site.
Admin
Christine says
I cannot get in to my WordPress website. I spoke with the server’s tech support and they said the problem is not on their end, and they suspect the site has been compromised by malware. However, I am not able to log in the site to check anything. Any advice?
WPBeginner Support says
Hey Christine,
Have you tried resetting password? Also see our guide on what to do when you are locked out of admin area.
Admin
greekouzina says
Hi all,
my website was hacked and i found many .php files like kebin.php kevin.php with eval and base64 code inside.
The worst thing is that my site was blacklisted and also the external references to the link are so many!
I noticed about 5 foreign IP’s that look into that reference files!
What can i do to cut off these references?
I have sucuri free version cause my blog is amateur blog and i dont have money to spend.
TIA
WPBeginner Support says
Cleaning an infected website can be a bit difficult for most beginners. You can try steps mentioned in our guide on fixing your hacked WordPress site.
Admin
Sandy says
someone hacking my admin panel again and again. I recovered but still he is hacking my admin-panel. I dnt know how to solve. Please kindly contact me for a solution.
Leo Dimilo says
Just got finished cleaning up a client’s website. One of the things that this article doesn’t address is the fact that you may have to go up a level in your server’s folder to find the backdoor. In other words, you could delete everything in your /html file on your server and restart with a fresh reinstall and still have a backdoor in because it is in a different folder on your server one level up….
Saad Amir says
Dear,
My website is hacked by someone. Only hack my posts, when i click on post for preview it would not be open, open as blank page.
Please help me, what is the main problem how i can solve it
WPBeginner Support says
Try switching to a default WordPress theme like twenty sixteen and deactivate all your WordPress plugins. Try to preview a post, if it opens fine, then your theme or one of the plugins on your website is causing the issue. If the problem persists, then follow the steps described above.
Admin
Joy Healey says
Hi,
This sounds to be really useful, but I’m struggling (on their website) to find the option you mention:
“They will monitor your site, and clean it up if you ever get hacked. It comes out to be like $3 per month per site if you get the 5 site plan.”
Could you point me in the right direction, please – with your affiliate link, of course?
Or perhaps it’s no longer available, which would be a shame – because that’s affordable, whereas all I’ve found at the moment is about $17 per month which is a bit of an ouch for more than one site
Thanks for a helpful article, Joy
Joy Healey says
Answering my own question above…. I checked with Sucuri and sadly the 5 site plan referred to in this post no longer exists.
Robin Jennings says
Great article- Sucuri is a fantastic program. It isn’t the cheapest option but they are onto issues within hours and a fix shortly after.
I’ve found a few exploits on clients website in the public_html/images file lately.
Thomas says
Hey there,
for guys who are familiar with ssh: what I do if there are hack problems is having backups ready for my complete websites and just compare the complete backup with the current state of the live project.
Still the corrupt files can be ‘sleeping’ in there for weeks or months, so it’s not 100% safe that one will find all the hack(ed) files, but it’s often a good indicator, where to look. This way I noticed 3 new files in a long time not updated avada(theme) project inside the revolution slider plugin.
Just my 2 cents :). Have a nice day,
Thomas
Jon Schear says
You can use the Sucuri scanner for free, but it is very complex with the results you get.
Rodney Wild says
Came across another signature: if(!isset($GLOBALS[“”\x61\156\x75\156\x61″”]
if you find the above statement, remove from the “if” right till the end of the line and that will fix that one file. I found this in almost every file though so you are going to have to use a global find and replace program. I use FNR.EXE but there are others. This one will also infect multiple websites in the same tree.
Kushal Jayswal says
Anyone noticed recent attack before a weak on major servers. I am using Hostgator hosting services. My sites were down for a day. One of my friend is using Bluehost and his sites were down for 4-5 days.
I couldn’t find news about this on Google.
Did anyone notice?
Michael says
Great Post, still relevant. I got malware the other day and downloaded my site to my computer. I sorted the files by “last modified” which showed me the pages that had been compromised.
I compared these files with backup files and was able to track down the malware!
Azman says
Nice post, I recently run exploit scanner and it found many malicious or suspecious codes in my site like eval and base64_decode. What should I do in this case do I need to setup my whole database from starting. I can do this because my site is not full of content.
But I am not very familiar with php, so help me.
WPBeginner Support says
Exploit scanner lets you know where it found the malicious code. If it is in a theme or plugin file, then you can simply delete those theme and plugin files. After that you can download and upload fresh copies of those files to your site. If it is in database and you can start fresh then do that. Other wise there are ways to clean the code from database too.
Admin
Dionisis Karampinis says
Very nice article many thanks! I have used Exploit Scanner and currently im having BPS Security
Matthew Baya says
Nice article. I’ve found on infected WP sites they consistently seem to put a file named https.php in the wp-includes folder. I also found on my shared hosting server they will hop from one infected account to find other world readable wp-config.php files in other WP installs and will use the database information there to create admin accounts on other WP installs. Thus I’d add that any one whose been hacked should change their database credentials and also lock down wp-config.php as much as possible, ideally limiting it so only the webserver user (and the owner) can access it.
I’ve been using wordfence to clean infected sites and have been very happy with is, though I recently found it’s no longer noticing the /wo-includes/https.php file I mentioned earlier. I’ve contacted them about this since i know in the past it did notice these
Nora McDougall-Collins says
I recent infection I had to deal with infected all the index.php files.
qammar says
Very helpfull and informative article.
one of my client website/blog was infected with malware was ‘reported attached page’ by google. first I tried sucuri sitecheck tool to identify the infected files/badware but they only show this result of scan
web site: blog.myclientwebsite.com/
status: Site blacklisted, malware not identified
web trust: Site blacklisted.
This do not any help, as we already know the site is black list and then I scan all the data on domain and found following two files infected
wp-includes\js\js\cnn.php
wp-includes\js\js\rconfig.php
I am posting this for other people to look for these files, if their website is infected and reported as attack page.
Cheers,
qammar feroz
Editorial Staff says
The free Sucuri scanner doesn’t do server side scanning. If you actually pay for Sucuri, not only it protects you, but they will do the cleanup for you if anything happens.
Admin
Nora McDougall-Collins says
Thanks for the excellent article! I have passed it along to my web development students through Facebook!
Also, one of my student’s site was hacked and shut down by the web host for the second time. It looks like he had being doing his database backups. So, it looks like we will have to copy and paste his posts directly into the Dashboard from the database dump. What fun!
Nora McDougall-Collins says
Sorry for the incomplete information – he had NOT been doing database backups. So, we will have to dump the database and copy and paste into the new install.
Patricio Proaño says
Excellent! Thank’s for the info, very useful!!
Pat Fortino says
You don’t have to pay securi anyting to scan your site. You can scan as many sites as you want for free. That scan will tell you where the hacks are.
Editorial Staff says
Not quite correct. Yes, they have a free scanner, but it only checks if the hacks have a front-end impact. For example, it will say that you have malware injections in your front-end, but it will NOT tell you where the backdoor is hiding and such. There are times that you might clean up the hacks results, but the backdoor still stays even after the cleanup. Then when it comes back, you are left to wonder why.
Admin
Andrew says
Nice guide. Have you looked at Wordfence (http://www.wordfence.com/)? I’ve put a lot of customers on to it and they rave about it.
Cheers,
Andrew
Editorial Staff says
Never needed to try it. Sucuri is highly recommended by many big brands. Having using them for a while, we can say that they are very good.
Admin
Gautam Doddmani says
thanks i am already using the plugin, eliminated many plugins because of it. real time scans are great and so is its firewall
Harry Candelario says
this was EXACTLY what I needed!! I’ve been trying to figure out how a hacker kept getting into one of the sites I maintain… it was just this one site, none of my other sites were being hacked. I found it with your help. It was hiding in a Pinterest plugin.
thanx again